What’s the difference between a Next Generation Firewall and a Web Application Firewall?
When it comes to protecting web applications we’re often asked: “Why use a web application firewall if there is a next generation firewall in place?” The short answer is, you need both.
So, what is a Web Application?
During the web’s infancy, websites were just static pages with very little user interaction. This changed in the 1990’s as web servers started to allow communication with server-side custom scripts [1], and developers now had the ability to build solutions such as web-based email, web stores and blogs. These are all examples of web applications, a program that is stored on a remote server and delivered over the internet through a browser [1].
Nowadays, web applications are more complicated, with a dependence on HTML5, JavaScript and databases etc. They may be a repository for corporate data, customer data or payment information and as a result have become an attractive target for attackers and must be secured correctly.
What is a Next Generation Firewall?
A NGFW combines the functions of a traditional firewall with additional features like intrusion detection and prevention, URL filtering, Antivirus/Anti malware, identity awareness, time-based decisions and location awareness.
Most importantly, a NGFW provides ‘application awareness.’ A traditional firewall is based solely on network-layer attributes (like IP address, port and protocol) but this is not enough information to accurately identify or police an application. A NGFW looks for abnormal information in the headers of a message and even within the data itself, and can be set to look for specific character strings (words or phrases) within the message body to identify an application. From there it makes context-based decisions on application traffic in order to protect the network, typically this would be internal users heading outside the network.
Protecting the Application Layer isn’t Enough
The issue here comes from the terms used by typical networking frameworks, in the OSI model for example the application layer is used to define “the collection of shared communications protocols and interface methods used by hosts in a communication network” [2], examples of which include HTTP, FTP, BitTorrent and SNTP.
Protecting the traditional application layer fails to fully protect an “application”. As shown in Figure 1, additional resources within infrastructure applications need protecting, such as web servers, business applications and application data.
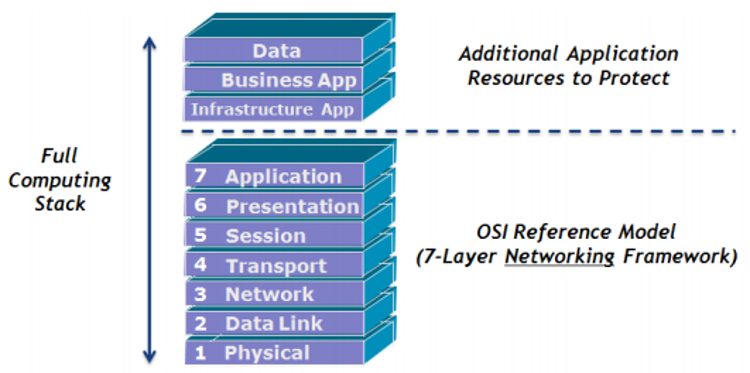
Figure 1 – The full computing stack model [3]
To protect Infrastructure apps, business apps and data, application fluency is required. Although a NGFW can identify an application regardless of the port and protocol being used this is not the same as application fluency, which needs the ability to truly understand how an application works rather than just what it is.
Enter the Web Application Firewall
A Web Application Firewall protects web servers and hosted web applications from threats at the highest level of the full computing stack and from non-volumetric attacks in the network layer.
WAFs are different from NGFWs in that they have the ability to:
- Provide DDoS protection at the application level
- Validate inputs (Stopping SQL injection)
- Provide cross site scripting protection
- Provide virtual patching to apps before vendors release official patches
- Block attacks based on known or custom defined application vulnerabilities
- Detect cookie and session tampering attacks
- Block unwanted web traffic from websites and applications
- Block potentially sensitive server responses from attackers
- Increase site speed and performance through advanced caching mechanisms
A WAF achieves critical application fluency in a few different ways. Many modern WAFs use automated learning to understand typical application behaviour over time, and as a result can differentiate between malicious and legitimate traffic. Manual configuration of application policies allows developers/ admins to tell the WAF exactly how their application works and the application fluency required to make decisions on traffic. High spec WAF’s and many cloud solutions will have the ability to conduct HTTPS decryption, enabling the WAF with deeper insights into application traffic. Couple these features with a default security capability and some business logic and it can make decisions a NGFW couldn’t on how to process web app traffic, which in turn grants them a greater level of protection.
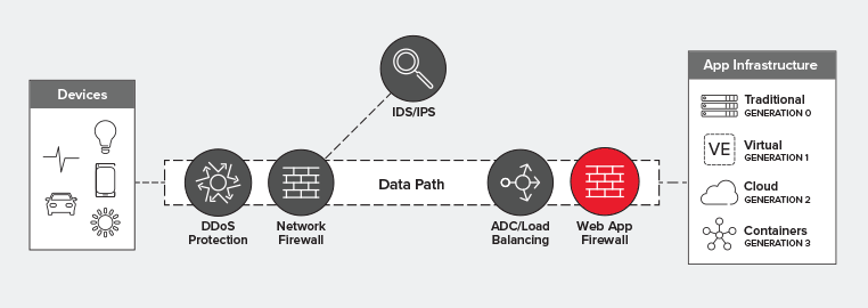
Figure 2 – A WAF in the Data Path [4]
WAFs are typically deployed inline, behind a traditional or next-gen firewall (See figure 2) functioning as a transparent reverse proxy or a reverse proxy. A transparent WAF allows traffic to be sent directly to the application server, whereas a non-transparent WAF will have a client’s traffic sent to it first and can provide greater protection to the application server, although often at the cost of performance.
References:
[1] https://securelink.net/en-be/insights/waf-vs-ngfw/
[2] https://osi-model.com/application-layer/
[4] https://www.f5.com/company/blog/where-does-a-waf-fit-in-the-data-path
VCG proud to support the NHS Nightingale Hospital at the NEC
Two weeks ago, VCG was asked by our client, The NEC, to help design and provide a completely new network for the emergency deployment of the NHS Nightingale Hospital at their Birmingham site in response to Covid-19.
NHS Nightingale Birmingham provides an additional facility for patients with Covid-19, helping to ensure there is enough critical care capacity within the system. The day 1 facility will initially provide 500 beds, with the capacity to scale up to 4,000 beds.
Axonex were already working with The NEC on a number of projects, including a network transformation project across their entire UK estate. To help the NEC in their additional requirement for NHS Nightingale, we were approached to deliver a network that was both scalable to support the required capacity but also a fully resilient, medical-grade solution.
Setting up these facilities is an enormous organizational challenge. Alongside the NEC, University Hospital Birmingham, MOD and other providers, the VCG team worked to have the network solution up and running in less than two weeks.
We’re immensely proud of the VCG engineers and project team who have dedicated their professional and personal time to install over 150 network switches connected to new structured cabling in just 7 days.

Image: The VCG team on-site at the NEC
VCG have worked closely with the NEC and Cisco UK team to utilise the latest network technology with Cisco DNA (Digital Network Architecture). The VCG NOC team will provide on-going support to the NEC IT team, supporting their team to ensure critical services remain live and support the hospital in its full capacity.
“In difficult times, it’s been fantastic to see the teams at VCG and The NEC dedicate themselves to this project. I am immensely proud of our team for their support and dedication, especially given the risks around social distancing during these worrying times.
Yet we know our role is a small piece of the puzzle compared to all the medical staff on the frontline and many others working around the clock to complete a project that would normally take months, even years. These organisations and individuals have come together to work collaboratively as we work towards the collective goal.
Our admiration and respect go to all the medical staff dedicated in providing the highest standard of care to those that desperately need their help in these difficult times.”
Andy Peters-Smith, VCG
Remote working: what you need to know

Now that homeworking is here to stay, we explore the essential technology and internet access for enabling robust remote working.
The world seems very different than it did in January. Ever since the lockdown started on March 23rd, the entire economy has found significant challenges in enabling teams to work from home for the foreseeable future, especially around productivity, security, resiliency and collaboration.
Finding novel solutions to these problems will help businesses in the long run, not only to increase the agility of businesses, but improve productivity too, though, only if the right foundations are put in place first.
As the dust is starting to settle, we’re beginning to get a clearer idea of what our customers will need in the short and long-term, to ensure businesses can carry on thriving, even through these tumultuous times. But one thing is for sure: homeworking is here to stay.
During this period of unpredictability UK businesses have been forced to adapt to homeworking and some have adapted better than others. For most it’s been a matter of trial and error and seeing what works for each individual operation.
So, here’s some top tips for adapting to a successful homeworking strategy.
1. Choose scalable connectivity
Your team now has all the physical hardware it needs – laptops, video conferencing software, wrist rests and second screens – so, that’s mission accomplished, right? Wrong.
Your homeworker’s communication is only as effective as the internet connection it runs through and the residential connections we all rely on for our iPlayer, YouTube, browsing and gaming are just not fast, reliable or secure enough to handle business usage.
Internet services for businesses are usually built to include a number of device and network-level security features to protect operations from malicious sites, hackers and misuse.
Considering that homeworking seems here to stay, it’s time to look further afield than just the office’s connectivity and look to bring remote worker’s internet connections in line with those used at larger office sites, because there are plenty of benefits, other than security that your team will be able to take advantage of.
Supporting homeworkers is an important consideration for businesses looking to protect their future success and by broadening the scope of your network to your team’s home offices, you can take back control of your system’s performance and gain a more detailed insight into team performance and the efficiency of your operation.
2. Collaboration with clarity
While businesses need to ensure homeworkers don’t fall victim to endless meetings and video calls in the name of ‘clear communication’, they do need to provide connectivity that supports high usage, while face-to-face contact is not an option.
Keeping staff morale high is important, especially at times like this. So, look for tools that enable your workers to communicate in different and more personal ways. IM software like Slack, Microsoft Teams, and MiCollab, are perfect for quick conversations with more involved, personable dialogue and the option to include emojis and GIFs, making communication more enjoyable and more responsive than traditional email.
Collaborative tools like virtual retro boards, workshop facilitators, and live polls and Q&As, keep staff engaged during town halls too, so make sure you’re using the right tools for the task at hand!
As some return to the office part-time, we will start to see more hybrid meetings, with some office attendees, and others from home. Therefore, it’s even more essential to get the process correct to ensure remote employees feel involved and part of the team, while ‘on site’ employees will require equal access to the tech they’ve been using at home.
3. Expect distraction and work around it
As you may be aware, childcare continues to be a challenge for many employees …
It’s an issue that employers can help overcome. By making time for regular check-ins that accommodate individual circumstances, employees can work around their existing constraints, so set your expectations and offer flexible ways for staff to meet them.
One person might prefer a check-in email at the end of the day, or another may like to correspond over IM throughout the day. As long as you’re considering their home/life balance when working out deadlines, then you should keep your team happy and (relatively) stress-free.
Keeping in touch is more important than ever but, with a rich stack of tech in place, you can host quick and effective check-ins with the different members of your team. Collaboration platforms like Microsoft Teams and MiCollab allow people to see when each other are busy or when they’re in calls. This enables workers to better use their time, not calling colleagues that are already in meetings, or on lunch, for example.
Ultimately, by allowing staff to take better and more control over their time and providing with the right tools to assess their teams and operations, business can become more productive with a robust homeworking policy and our products and services can enable you to do just that, so get in touch and discover how we can help you adapt to the new normal of the economy.
Superior Technology to maintain efficiency
SLAs
If the internet goes down at the office, you lose money, so quick fixes are essential and the same goes for your homeworkers too. Internet outages on residential lines have no guaranteed timescales for a fix, which could mean hours, days or even weeks of lost productivity for staff. Business connections mean fast fixes within the agreed Service Level Agreement (SLA) guarantee.
Better Bandwidth
While consumer download speeds are usually up-to-task, upload speeds are often overlooked. As video calling and VoIP calls are reliant on both upload and download speeds, they’re key to collaborating in real-time for your staff.
Reliable Remote Management
Remote employees may require secure VPNs to access central information and business can’t manage an employees’ residential connection as its completely separate from the business. Therefore, Static Ips and strong remote management features are essential features, unique to business connections. They’re also perfect for running fixed assets like CCTV and alarms systems, that again can be managed remotely.
For more information or to discuss your requirements in detail, please get in touch with our team today.
Secure remote working – how VCG is helping customers
In response to COVID-19 organisations are moving their workforce to the virtual workspace. The speediness of this rollout by our customers has been fantastic.
The first step taken by IT teams has been to quickly enable the workforce to access corporate resources when working from home, when they need to. However, with the speed and scale of this roll out, protecting your remote workers is a challenge.
In this blog we’ll outline some of the key security considerations and how VCG are helping customers work not just remotely, but securely, and how to prevent breaches at a time of increased risk.
Secure VPN access
A VPN client like Cisco AnyConnect will help ensure end-to-end encryption, prevent man in the middle attacks and ensure data integrity, but there are some additional decisions that need to be considered.
Some organisations will send all user internet activity (corporate and non-corporate) back through the corporate firewall for deeper inspection, malware analysis and content classification etc. While this is secure, it effectively doubles the bandwidth for a single remote user vs. an office user. As a result, many customers are now finding the Internet connection to be a bottleneck.
To ease bandwidth congestion organisations can forward only corporate requests via the secure VPN connection. Great, but how do you ensure your users are protected from accessing non-corporate domains on the internet that could pose a risk to them and the data they can access, or from using unapproved applications or accessing sites in breach of corporate usage policy?
Protect users everywhere with DNS security
The answer here is Cisco Umbrella. Umbrella provides security for users at the DNS layer, forwarding all DNS requests to Umbrella to identify whether a domains content category is associated with malicious intent (such as phishing, malware, crypto-mining, command and control etc). If so, Umbrella will block access to these sites before the user can connect. As Umbrella is a cloud delivered service, and with no required connection to the corporate VPN, your users will be protected whether working from home or from the local coffee shop (when they re-open).
Verify the identity of your users
Finally, we have the question of user verification and device posturing. The last thing you want is a misplaced corporate laptop or stolen log on credentials to be able to access your network via the VPN, or a device that is vulnerable through outdated operating systems, browsers or anti-virus potentially causing a breach. Cisco Duo enables both Multi-Factor Authentication (MFA) and device posturing. With these in place, when a user enters their credentials, they will also be prompted for a second input such as a code via text, a call to a mobile device with authentication or as simple as a push notification via the Duo App to a registered smartphone. Duo can also confirm operating system, browser and anti-virus are all up to date before permitting access, and if not up to date, inform the user on the actions that need to be carried out in order to gain access.
Trial Umbrella and DUO for your business
To see how these solutions can improve your security posture for remote workers, VCG can help you set up free software trials of Cisco security solutions within your own organisation and environment.
How smart is your warehouse? Six ways IoT connectivity can raise your retail game and drive sales

IoT will help you get omnichannel match fit
Modern omnichannel customers have incredibly high expectations. They take it for granted the products advertised in-store and online are immediately available and they want their order fulfilled through the most convenient channels and with the absolute minimum of delay.
This has long been a stumbling block for brick-and-mortar retailers looking to sell online, but smart tag solutions now provide an answer. IoT warehouse technology such as RFID gives the retailer a highly accurate real-time view of the number and location of SKUs they have in stock across their estate. This means both the retailer and customer can be confident that displayed stock levels are accurate. The retailer can locate SKUs immediately and fulfil orders in a fraction of the time.
Fashion retailer River Island is just one of many stores that attach RFID tags to all of their stock. Prior to RFID, River Island was achieving a stock accuracy level of around 70%, but this is now as high as 98%. Meanwhile Marks and Spencer has reported a 5.5% increase in sales following its adoption of RFID.
RFID tags can store considerably larger data volumes than barcodes. This includes SKU size, manufacturer, expiration date, serial number, production line, and so on. An average RFID reader also has a higher speed than a barcode reader and can scan up to 200 tags at once.
Accurate IoT fulfilment opens up a world of alternative omnichannel distribution models – potentially turning any store or warehouse into a distribution hub or converting uneconomical retail outlets into so-called ‘dark store’ mini fulfilment centres.
IoT boosts warehouse productivity
Warehouse management systems (WMS) are widely used by retailers to monitor inventory-related activities, but most are driven by ERP systems which rely on time-consuming, labour-intensive and error-prone processes. When IoT devices are integrated into a WMS however, they take warehouse management to the next level. That’s because smart warehouse solutions are designed to monitor inventory, gather data and generate tasks accurately, autonomously and fast.
Warehouse data is accurately harvested, processed and analysed within seconds before a condensed inventory (or other warehouse-related data) is shared with the end-user via a user-friendly dashboard.
This warehouse data can be used alongside real-time customer orders to automate and streamline warehouse tasking and workforce allocation. Various workforce management systems use artificial intelligence to calculate the most efficient way of picking orders and they then task employees via smartwatches, mobile phones and tablets. Employee performance can also be monitored and incentivised to ensure the best results.
Get to grips with perishable stock damage and waste
The UN Food and Agriculture Organization states that one-third of all foods perish in transit as supply chain managers fail to create proper storage conditions during transportation and delivery. That’s bad news for retailer profits and bad news for the planet.
IoT systems for warehouses and transportation can track and automatically adjust the temperature, atmospheric pressure, moisture, and other properties that could jeopardize the integrity of transported goods. They can also accurately monitor sell-by dates and ensure the right stock hits the shop floor at the best possible moment, protecting profits and increasing customer satisfaction.
Ensure warehouse business continuity with predictive maintenance
Modern warehouses rely on a complex array of systems to ensure the best storage conditions for stock, as well as a safe and productive working environment for employees. These systems include refrigeration units, lighting and heating, ventilation and air conditioning (HVAC) to name but a few.
These systems can quickly waste money if they’re not managed properly and they can even halt operations if they fail. When warehouse hardware is equipped with IoT smart sensors however, the data can be used to instantly detect failures or performance issues. Artificial intelligence can also interrogate this data and predict when equipment failure is likely to happen, so that pre-emptive maintenance can prevent unnecessary expense and unplanned downtime.
Take full control of your supply and distribution chains
A warehouse capable of tracking stock levels in real time right down to individual SKUs gives retailers a powerful opportunity to reimagine their supply chains.
For a start, high-confidence IoT-generated data means retailers can switch to a lean supply chain model, reducing their on-premise stock levels and significantly cutting costs. It also means that retailers can switch to a demand-driven, customer-centric supply model more easily – stocking what they sell, rather than attempting to sell what they stock.
This achieved by monitoring customers’ buying signals the length of their path to purchase and translating these signals in real time to warehouse actions. This could mean, for example, ordering more stock from suppliers, fulfilling orders faster, locating SKUs across the retailers estate to name but a few.
IoT-generated warehouse data also enables retailers to keep a closer eye on supplier performance and identify potential supply chain bottlenecks before they escalate. For instance, this can be achieved by monitoring and collecting data on late and incorrect deliveries so they can be raised with a supplier in a timely manner.
Pioneer innovative retail models with the help of IoT
Granular IoT-generated warehouse data can enable retailers to become significantly more innovative with their inventories and assortments. For example greater IoT-driven fulfilment speed and agility in the warehouse makes it possible to support in-season capsule collections in fashion retail, pop-up stores which may only trade for a month or two and stores which change their inventory on a regular basis. Nike’s LA concept store is one such example. It’s store assortment changes every two weeks and is based on local NikePlus members’ online browsing and purchasing behaviour.
Contact VCG to find out if your digital networks are robust and secure enough to support IoT devices and deliver the benefits of a smart warehouse. Connecting to cloud solutions does increase cybersecurity risk, but VCG provides the additional protection your network needs. We also offer solutions to ensure your brand is fully connected and your network is scalable, flexible and can be fully managed with 24/7 service and technical support. Get in touch to find out how we can help your business grow.
VCG boost Customer Success Practice with Cisco’s Advanced Customer Experience Specialization
The right IT solution has been planned, purchased, configured, delivered and implemented on time, but has the wider business perceived the investment as a success? Actually, many businesses will never see the full value of their IT investments from their solutions providers. With a transition to more cloud-based services and OPEX investments, the gap between the ‘potential’ outcome (whether that’s user adoption, feature adoption, meeting time frames for deployment etc.) vs. ‘actual’ is growing as organisations struggle to effectively adopt new cloud technologies. That’s where customer success comes in.
So, what exactly does customer success mean for VCG, and more importantly, to our customers?
Put simply, customer success is a business methodology that ensures our customers get the most from VCG products and services. It starts by asking ‘WHY?’ What is driving this business change? From there, we use consistent, process-driven engagements, along with real-time data, analytics and automation to bring those business goals to reality, from point of purchase, through to technology adoption and renewals. To make this happen, VCG have made significant investments internally in training, process optimisation, and a suite of new tools, combined with 15 years of industry experience.
This isn’t limited to new products or solutions; we understand business use cases change, and we review existing solution deployments to ensure our customers are adopting all of the relevant features and functionalities in the right way, and help them to expand these solutions successfully within their business. We also delivery regular technology strategies and roadmaps to ensure our customers have a clear vision.
We’re pleased to say that VCG are one of only few Cisco partners to achieve Cisco’s Advanced Customer Experience Specialization. With this accreditation VCG have demonstrated the ability to provide the highest level of service across all Cisco technologies and integrate this throughout our existing Customer Success Practice.
Email - friend or foe?
Email is probably the most widely used and important business tool for communication, and you won’t be surprised to hear that emails are the most used vector for cyber-attacks, and are also the primary method of spreading malware.
The end user is often referred to as the weakest link in the chain, and while it’s probably fair to say that employee awareness and prevention today is higher than ever, it’s also true that attackers are using more sophisticated and highly targeted techniques to breach the wall. In a digital environment where emails are sent from anywhere and on any device, organisations need a robust defense in place and that guards against spam, social engineering & phishing, fraudulent senders, infected files, and blocks risky URLS. Users don’t want to be continuously mining through a library of emails sorting the good from the bad, and employers don’t want them to focus on this in-efficient and risk inherent process.
What level of risk do emails present to organisations? We took a view of one of our customers to find out. A global brand and leader in their field, this customer has Cisco Cloud Email Security deployed globally across 60+ countries and 10,500+ users.
| INCOMING MAIL SUMMARY | ||
| Message category | % | Message Volume |
| Stopped by Reputation Filtering | 79.0% | 146.4M |
| Stopped as Invalid Recipients | 0.3% | 641.7k |
| Spam Detected | 0.9% | 1.7M |
| Virus Detected | <0.01% | 3,491 |
| Detected by Advanced Malware Protection | <0.01% | 1,295 |
| Messages with Malicious URLs | 0.1% | 95.5k |
| Stopped by Content Filter | 0.2% | 332.6k |
| Total Threat Messages | 80.5% | 149.0M |
| Marketing Messages | 2.0% | 3.7M |
| Social Networking Messages | 0.2% | 346.0k |
| Bulk Messages | 1.5% | 2.7M |
| Total Graymails | 3.7% | 6.8M |
| Clean Messages | 15.9% | 29.4M |
| TOTAL ATTEMPTED MESSAGES – 185.2M | ||
What do the results tell us?
Firstly, a staggering 80.5% (146.9 million!) of all emails represent a threat and have been blocked. A figure of 3.7% graymails leads you to truly appreciate how big this percentage is (these emails seem to fill our inbox quicker than any other) and this stat demonstrates just how far the protective net needs to be cast. In fact, only 15.9% of emails are ‘clean.’
Secondly, the vast majority of ‘Threat Messages’ are ‘Stopped by Reputation Filtering’ and this is where Cisco Email Security steps ahead of the competition with its comprehensive threat intelligence from Cisco TALOS – one of the largest threat detection teams in the world providing real time global threat intelligence, identity and relationship modelling, and behaviour analytics from a wide range of sources, including 600 billion messages, 16 billion web requests, and 1.5 million malware samples daily.
And third – While prevention here has mitigated the other 99.99+% of the risk, there is no security solution available that can guarantee 100% prevention and a layered approach should always be put in place to analyse file activity across the extended network and to quickly detect, contain, and remove advanced malware if it gets through. In this instance <0.01% of threats required detection by Cisco’s Malware prevention tool (Advanced Malware Prevention).
The verdict? By their nature or reputation, some organisations are naturally bigger targets than others, and while these figures may not translate exactly to every organisation, it demonstrates a very real threat platform and one that every organisation will encounter. Email security from the cloud is essential and needs to deliver comprehensive threat intelligence, reputation filtering, antispam filtering, forged email detection, phishing prevention, Mailbox Auto-Remediation, and post breach advanced malware protection.
If you’d like to talk email security, our experienced team are happy to assist. If you want to see how these stats look for your organisation, VCG can offer a free trial of Cisco Cloud Email Security for 45 days.
Endpoint security. Start at the DNS
Borderless networks are nothing new – we’ve heard about them for years. Users can connect to corporate resources on any device, from anywhere. Yet, for the first time, Cisco have a security solution that can truly claim to offer full security enforcement for a borderless network. That solution is Umbrella.
Umbrella positions itself perfectly by securing one of the fundamental building blocks of network communications – DNS. Almost all communications over the Internet, whether they are deliberately invoked by a user or silently invoked by applications, require a DNS lookup. Therefore, if you can accurately secure the DNS layer, you can accurately secure almost all network communications. If you can do this for users both on and off the corporate network then you are covering all of your blind-spots.
Yet this approach only works if the decisions you make are accurate. Originally developed by OpenDNS, this is where Umbrella steps up. From the outset, the solution has been built into the fabric of the Internet through close peering relationships with ISPs which result in Umbrella collecting enormous amounts of data on a daily basis (approximately 100 Billion requests per day!). This information is processed through industry-leading algorithms and data-processing tools to provide highly accurate information about which requests should be allowed or blocked. If a DNS request is blocked, users and, more importantly, malicious applications cannot (in most cases) access a malicious resource. Quite often, blocking network communications for a piece of malware is as effective as removing the malware completely.
As well as securing network traffic, Umbrella enforces your IT policy by controlling access to content deemed inappropriate for an organisation – essentially performing the job of a web proxy but with two crucial advantages: firstly, the majority of traffic will not need to be proxied (bad stuff is blocked, good stuff is allowed, all at the DNS level) making the solution scalable, high performing and less likely to break cloud-based applications; secondly we’re not just talking about web requests here – DNS, and therefore Umbrella, cover all requests regardless of application or protocol. Further to this, if Umbrella isn’t 100% sure that a site is safe, it automatically redirects web traffic to Umbrella’s towers and WILL proxy that traffic so that malware scanning can take place and ensure no infection.
So, there must be a catch somewhere, right? Actually, there isn’t. Umbrella is incredibly easy to integrate into existing networks. In some cases, it is as simple as changing from using your existing ISP DNS servers for external lookups to using Umbrella’s servers. This simple change can be enough to secure entire networks in minutes. Even mobile devices can be protected using the Umbrella App.
The bottom line is this: you are already using DNS for virtually everything you do online – given the choice, why wouldn’t you choose to protect it?
Learn more about Cisco Umbrella with a free, no obligation trial.